Writeup: FlareOn 2021: 001 - credchecker
1. TLDR
2. Input data
The challenge file is here. Password: flare.
The subject of the task is an html page with embedded javascript. The available files are:
admin.html
img/goldenticket.png
img/logo.png
Due to the fact that the implementation of the program logic is located in the admin.html file, it is sufficient to limit ourselves to analyzing this file.
3. User interface
Access to the panel is protected:
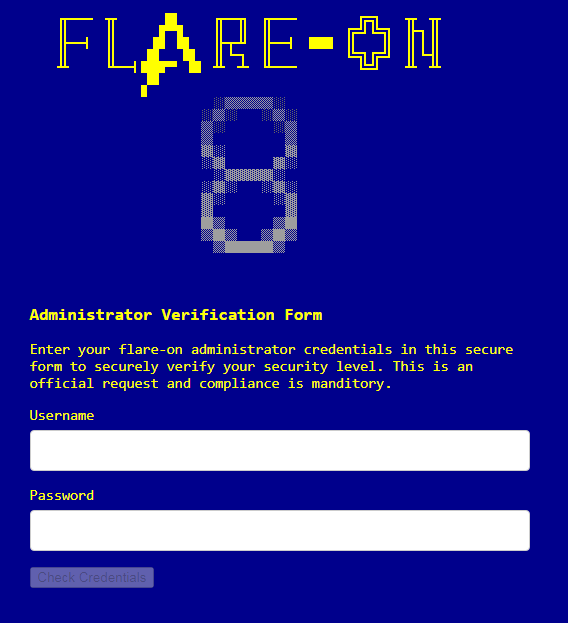
Therefore, an attempt should be made to analyze the method of verification of credentials
4. Code analysis
In the source of the page, you can find a code snippet that verifies credentials:
function checkCreds() {
if (username.value == "Admin" && atob(password.value) == "goldenticket")
{
var key = atob(encoded_key);
var flag = "";
for (let i = 0; i < key.length; i++)
{
flag += String.fromCharCode(key.charCodeAt(i) ^ password.value.charCodeAt(i % password.value.length))
}
document.getElementById("banner").style.display = "none";
document.getElementById("formdiv").style.display = "none";
document.getElementById("message").style.display = "none";
document.getElementById("final_flag").innerText = flag;
document.getElementById("winner").style.display = "block";
}
else
{
document.getElementById("message").style.display = "block";
}
}
You can see that the expected username is Admin. The password, on the other hand, should be a base64-encoded string goldenticket.
The password is the result of the function:
btoa("goldenticket")
therefore the password is:
Z29sZGVudGlja2V0
5. Reading the flag
After entering the correct data, you can read the flag:

enter_the_funhouse@flare-on.com