Writeup: FlareOn 2022: 004 - darn_mice
1. TLDR

2. Input data
The challenge file is here. Password: flare.
The subject of the task was the PE file:
darn_mice.exe
3. Initial analysis
I verified the file type of darn_mice.exe :
$ file darn_mice.exe
darn_mice.exe: PE32 executable (console) Intel 80386, for MS Windows
Running the console program darn_mice.exe did not indicate any user interaction.
After entering a test parameter into the program, the standard output showed text and the program ended with an unexpected error:
>darn_mice.exe flare
On your plate, you see four olives.
You leave the room, and a mouse EATS one!
I then loaded the program into the IDA environment
4. Code analysis
A quick analysis of the code revealed that the ciphertext and the RC4 algorithm should be tackled again.
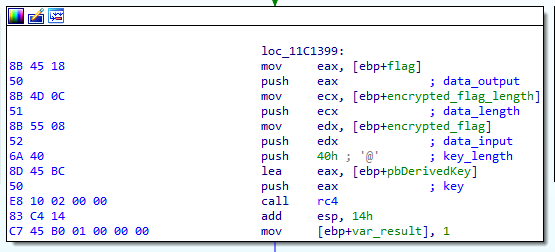
In order to decrypt the flag, the password had to be given as an argument to the program. The password just before decrypting the flag was expanded to the correct rc4 key using a salt of salty and the PBKDF2-HMAC-SHA512 algorithm.
There was another problem: the password had to be shorter than 36 characters and was subject to verification.
Verification consisted of decrypting the password with an affine cipher (p[i]+k[i]) mod 256 with a fixed, fixed key:
50 5e 5e a3 4f 5b 51 5e 5e 97 a3 80 90 a3 80 90 a3 80 90 a3 80 90 a3 80 90 a3 80 90 a3 80 90 a2 a3 6b 7f 00
Each byte of the password after decryption had to be a valid shellcode that could be run in the format:
shellcode(shellcode)
5. Generate ciphertext
The selected plaintext was the RETN command (0xC3). So I developed a script that would generate a password for the program, which would generate a byte string (plain text) 0xC3
from malduck import xor
key = b"\x50\x5e\x5e\xa3\x4f\x5b\x51\x5e\x5e\x97\xa3\x80\x90\xa3\x80\x90\xa3\x80\x90\xa3\x80\x90\xa3\x80\x90\xa3\x80\x90\xa3\x80\x90\xa2\xa3\x6b\x7f"
plaintext = b'\xc3'*35 # RETN
ciphertext = ''.join([chr(p-k) for (k,p) in zip(key,plaintext)])
print(ciphertext)
Po uruchomieniu otrzymałem hasło do programu (szyfrogram):
see three, C3 C3 C3 C3 C3 C3 C3! XD
6. Reading the flag
I run the program given the designated argument:
> .\darn_mice.exe "see three, C3 C3 C3 C3 C3 C3 C3! XD"
On your plate, you see four olives.
You leave the room, and a mouse EATS one!
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
Nibble...
When you return, you only: see three, C3 C3 C3 C3 C3 C3 C3! XD
i_w0uld_l1k3_to_RETurn_this_joke@flare-on.com
Thus, the flag is:
i_w0uld_l1k3_to_RETurn_this_joke@flare-on.com