Writeup: FlareOn 2022: 010 - Nur geträumt
1. TLDR

2. Input data
The challenge file is here. Password: flare.
The subject of the task were files:
Nur geträumt.img
README.txt
I verified the file type Nur geträumt.img:
$ file Nur\ geträumt.img
Nur getra\314\210umt.i: Apple DiskCopy 4.2 image Nur getr\212umt, 1474560 bytes, MFM CAV dshd (1440k), 0x2 format
The file README.txt contained a message:
This challenge is a Macintosh disk image (Disk Copy 4.2 format, for those who need to
know) containing a 68K Macintosh program. You must determine the passphrase used to
decode the flag contained within the application. Super ResEdit, an augmented version of
Apple's ResEdit resource editor which adds a disassembler, is also included on the disk
image to help you complete the challenge, though you will likely also need to do some
outside research to guess the passphrase.
This application can be run on any Macintosh emulator (or any real Macintosh from as far
back as a Mac Plus running System 6.0.x up to a G5 running Classic). The setup of the
emulation environment is part of the challenge, so few spoilers live here, but if you
want to save yourself some headaches, Mini vMac is a pretty good choice that doesn't take
much effort to get up and running compared to some other options.
This application was written on a Power Macintosh 7300 using CodeWarrior Pro 5, ResEdit,
and Resourcerer (my old setup from roughly 1997, still alive!). It was tested on a great
many machines and emulators, and validated to run well on Mac OS from 6.0.8 through 10.4.
Happy solving! Be curious!
3. Initial analysis
I made an attempt to extract the file Nur geträumt.img. To do so, I downloaded the Convert2Dsk utility. Convert2Dsk is an application for converting Disk Copy 4.2 images to raw disk images:
>convert2dsk.exe ".\Nur getraůumt.img"
Converting ".\Nur geträumt.img"... success!
I then loaded the disk image into the FTK Imager tool:
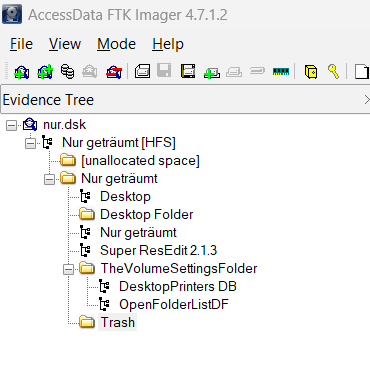
At this stage, I found nothing relevant. I decided to install and configure the emulator.
4. Installation and configuration of the emulator
Using instructions found on YouTube, I performed the following configuration.
I completed the process with a prepared Mini vMac
5. Disk content analysis
I mounted the file Nur geträumt.dsk (I changed the original name of the file and directory because of problems loading into the emulator).
Two files were visible:
- Application
Nur geträumt. - The
Super ResEdit 2.1.3utility.
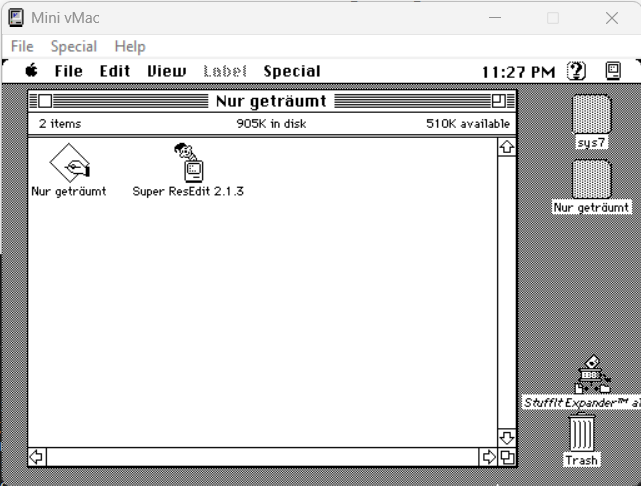
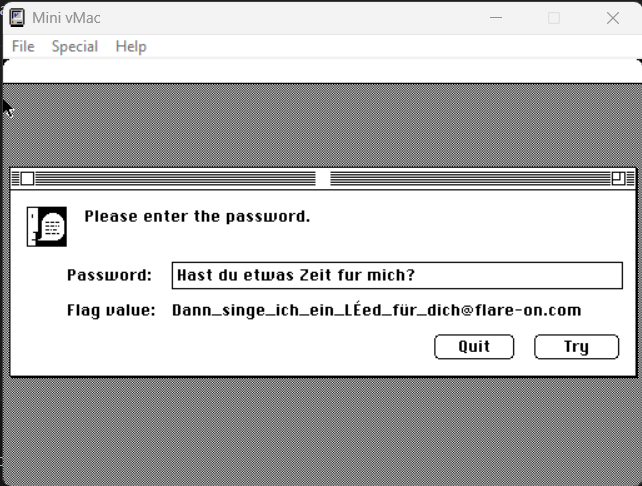
After running the program Nur geträumt, a window was displayed with a message prompting the user to enter a password:
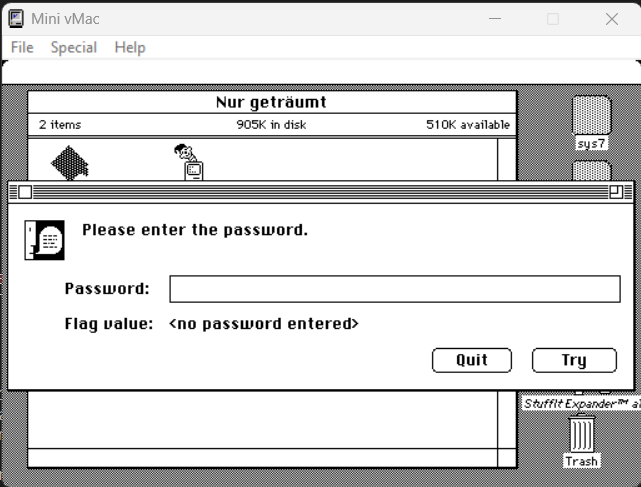
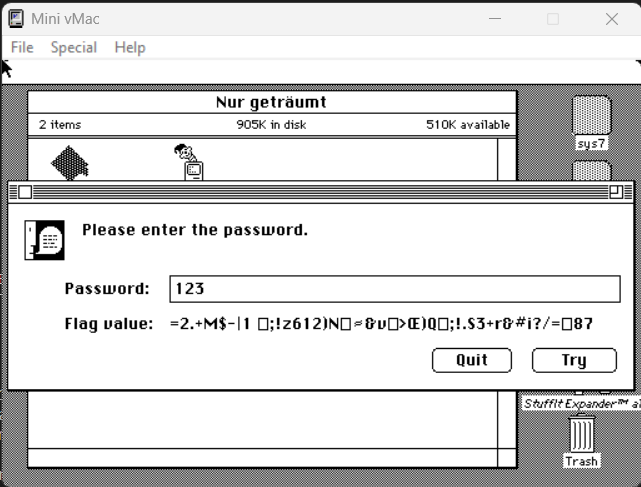
After entering a random password, a random text string was presented:
6. File analysis
I loaded the program file into the Super ResEdit 2.1.3 utility:
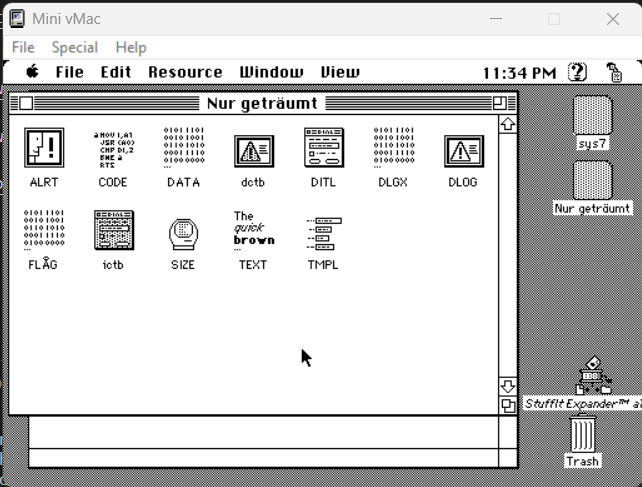
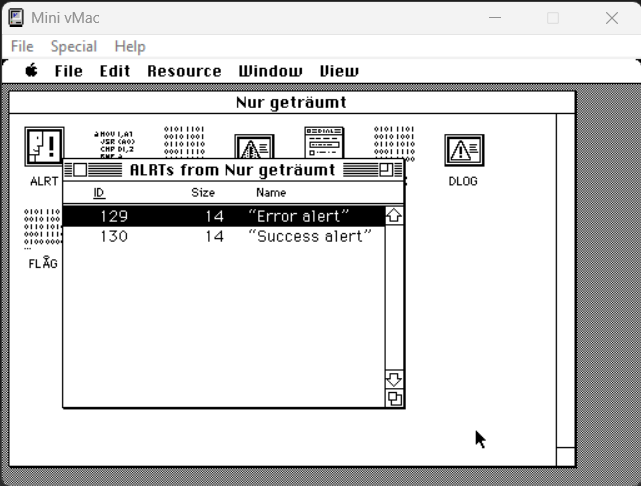
The application had 2 alerts defined:
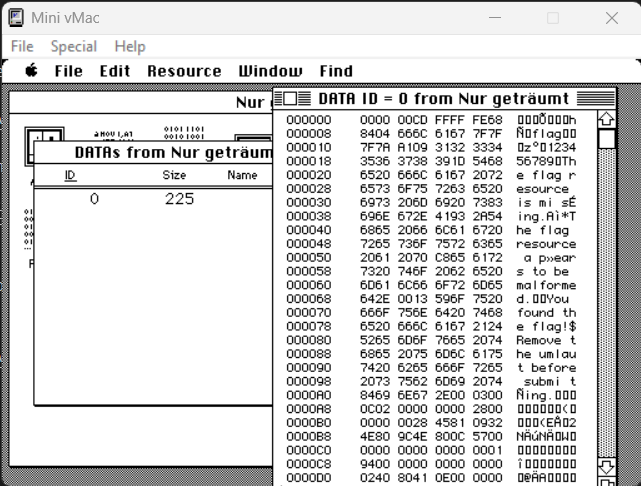
The application had 1 unnamed data block defined:
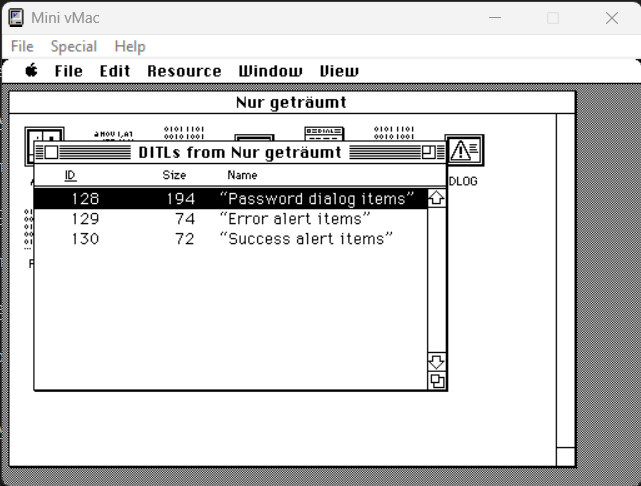
The application had 3 labels defined for the dialogs:
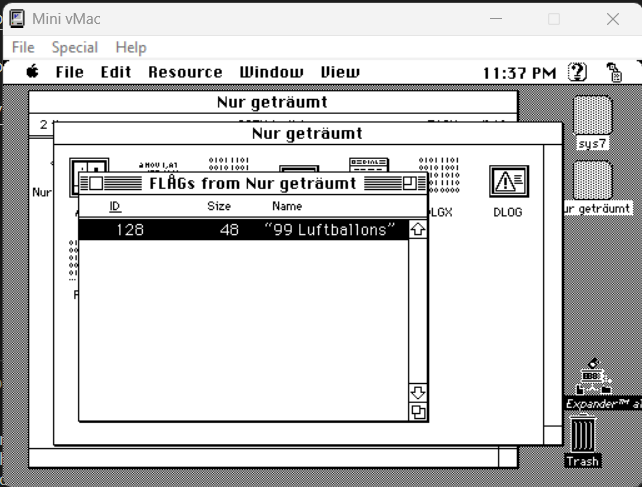
In addition, the application had defined an interesting resource FLAG:
The definition of the FLAG resource could be previewed in Super ResEdit 2.1.3:
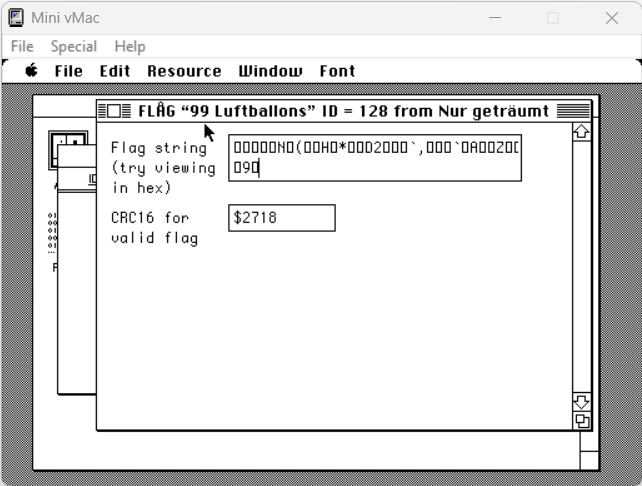
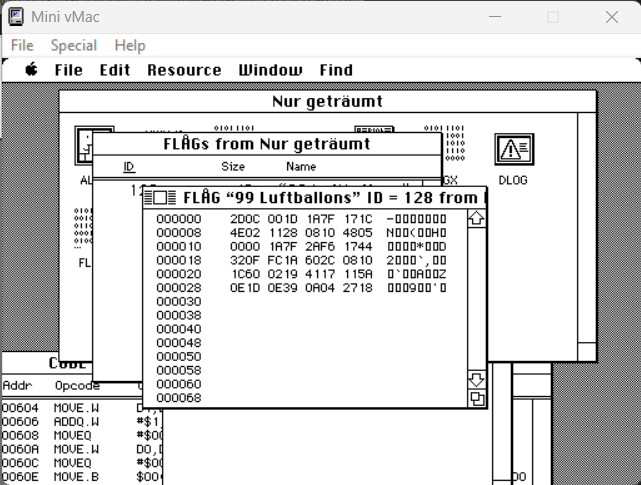
and read the individual values in the hex editor:
The analysis of the TMPL resource made it possible to determine the types of data:
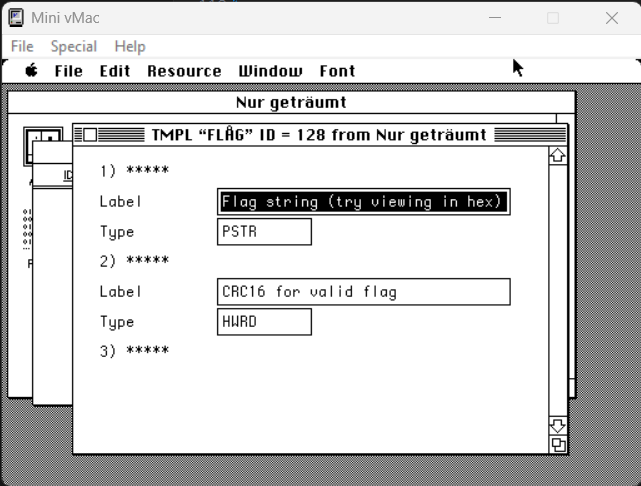
From reading ResEdit Reference For ResEdit 2.1, it is known that PSTR is Pascal string and HWRD is hex word:
So 0x30 is the size of the entire structure (48 bytes). 0x2D is the length of the Pascal string (45 bytes) and the last two bytes 27 18 are the CRC16 value:
In addition to the aforementioned elements, the application code, form factors and a large block of text were visible, among others:
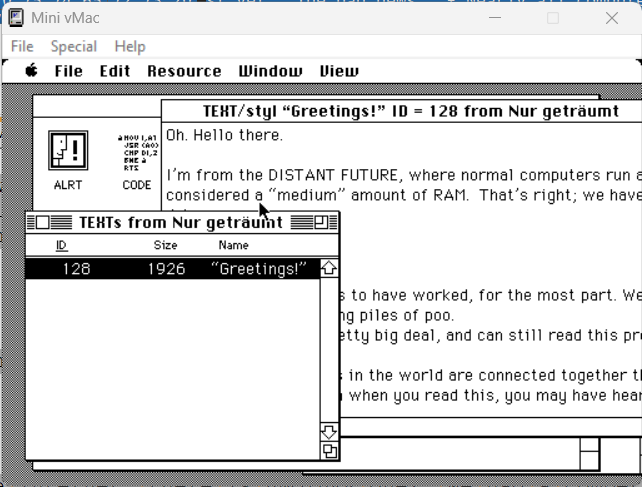
which included:
Hello there.
I'm from the DISTANT FUTURE, where normal computers run at 2-4 GHz and 16 GB is
considered a "medium" amount of RAM. That's right; we have more RAM than you
have hard drive space.
The good news:
- Unicode really seems to have worked, for the most part. We even have characters
for clown faces and smiling piles of poo.
- The Mac is still a pretty big deal, and can still read this program (but hasn't
been able to run it for a while).
- Nearly all computers in the world are connected together through a network
called the Internet. Depending on when you read this, you may have heard of it.
Don't get rid of MacTCP just yet.
The bad news:
- Nearly all computers in the world are connected together through a network
called the Internet. This has made a lot of people very angry and been widely
regarded as a bad move.
- Despite having 16 GB of RAM, Microsoft Word still takes up roughly half of it.
- We're still using Microsoft Word.
Anyway, because in the future we're stuck at home due to a worldwide pandemic
(no, not the Internet, there is ANOTHER one), we had a competition for finding
fun things in computer programs. I've hidden a flag in this program, but it's
not going to be all that easy to find just with ResEdit.
You'll probably need to interact with the program a bit. It will let you know
when you've found the right flag. I've done you the favor of including Super
ResEdit here, which has a disassembler, and I'm even nice enough to give you
the debug version of the program with all the symbol names, to give you a head
start (because I'm not wicked enough to make you step through it with MacsBug,
but you could if you wanted).
Here's your first hint: 1983 was a pretty good year in music.
Have fun, and enjoy the challenge!
- Dave Riley, July 2022
7. Executable code analysis
Analyzing the code in the program Super ResEdit I noticed the function decodeFlag:
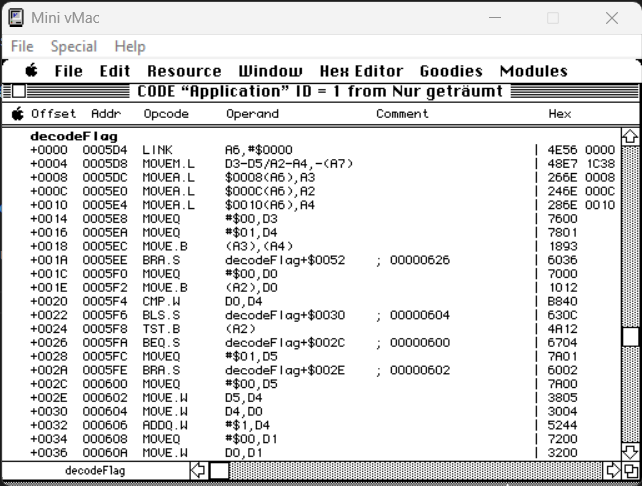
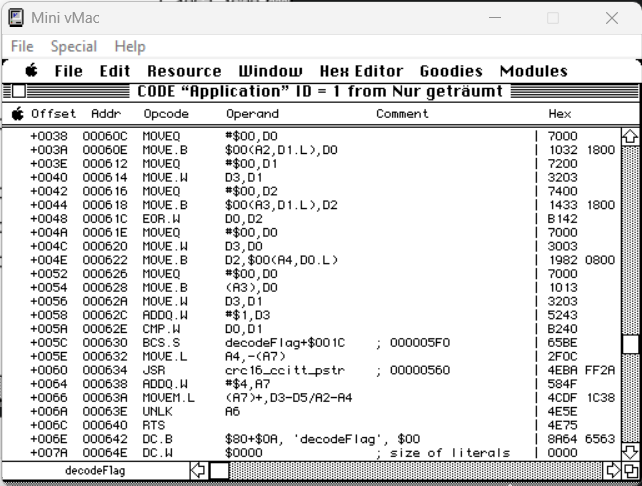
I noticed under offset ++048 the EOR.W command responsible for the XOR (Exclusive OR) operation.
8. Reading the flag
In order to read the flag, I made assumptions:
- the flag was encrypted with the OTP algorithm.
- the plaintext contains the postfix
@flare-on.com.
Knowing a piece of plain text, I made an attempt to recover part of the key:
import malduck
known_plaintext = "@flare-on.com"
msg_length = 0x2D
plaintext = (msg_length-len(known_plaintext))*'a'+known_plaintext
plaintext_bytes = plaintext.encode('latin1')
ciphertext_bytes = b'\x0C\x00\x1D\x1A\x7F\x17\x1C\x4E\x02\x11\x28\x08\x10\x48\x05\x00\x00\x1A\x7F\x2A\xF6\x17\x44\x32\x0F\xFC\x1A\x60\x2C\x08\x10\x1C\x60\x02\x19\x41\x17\x11\x5A\x0E\x1D\x0E\x39\x0A\x04'
key = malduck.xor(plaintext_bytes, ciphertext_bytes)
print(key)
In the standard output I read the text:
b'ma|{\x1ev}/cpIiq)daa{\x1eK\x97v%Sn\x9d{\x01Miq} du etwas Zei'
The visible fragment of the lyrics du etwas Zei was an excerpt from the song Neny from the album 99 Luftballons, which corresponded with the artifacts found in the app.
The first line of the lyrics of this song is:
Hast du etwas Zeit für mich?
I used this sentence as a key:
ciphertext_bytes = b'\x0C\x00\x1D\x1A\x7F\x17\x1C\x4E\x02\x11\x28\x08\x10\x48\x05\x00\x00\x1A\x7F\x2A\xF6\x17\x44\x32\x0F\xFC\x1A\x60\x2C\x08\x10\x1C\x60\x02\x19\x41\x17\x11\x5A\x0E\x1D\x0E\x39\x0A\x04'
key = 'Hast du etwas Zeit fur mich?'
key_bytes = key.encode('latin1')
plaintext_bytes = malduck.xor(key_bytes, ciphertext_bytes)
plaintext= plaintext_bytes.decode('latin1')
print(plaintext)
In the standard output I read the text:
Dann_singe_ich_ein_Led_fr_dich@flare-on.com
Entering the key into the program resulted in the reading of a flag: