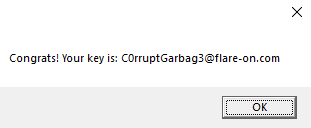
Writeup: FlareOn 2020: 002 - garbage
1. TLDR
2. Input data
The challenge file is here. Password: flare.
The only thing I got at the beginning of this task was a garbage.exe file
3. Inspection of garbage.exe
I verified the file with the tool file:
$ file garbage.exe
garbage.exe: PE32 executable (console) Intel 80386, for MS Windows, UPX compressed
The file was packaged with the UPX utility. I tried to unpack the file:
$ upx -d -o upx_removed.exe garbage.exe ✔ 20:07:48
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2020
UPX git-d7ba31+ Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
File size Ratio Format Name
-------------------- ------ ----------- -----------
upx: garbage.exe: OverlayException: invalid overlay size; file is possibly corrupt
Unpacked 1 file: 0 ok, 1 error.
Well, in the text of the task there was a note that the file was damaged.
I analyzed the file using the xxd utility:
$ xxd garbage.exe| less
...
00009e50: 0000 0000 0000 0000 6050 0100 3c3f 786d ........`P..<?xm
00009e60: 6c20 7665 7273 696f 6e3d 2731 2e30 2720 l version='1.0'
00009e70: 656e 636f 6469 6e67 3d27 5554 462d 3827 encoding='UTF-8'
00009e80: 2073 7461 6e64 616c 6f6e 653d 2779 6573 standalone='yes
00009e90: 273f 3e0d 0a3c 6173 7365 6d62 6c79 2078 '?>..<assembly x
00009ea0: 6d6c 6e73 3d27 7572 6e3a 7363 6865 6d61 mlns='urn:schema
00009eb0: 732d 6d69 6372 6f73 6f66 742d 636f 6d3a s-microsoft-com:
00009ec0: 6173 6d2e 7631 2720 6d61 6e69 6665 7374 asm.v1' manifest
00009ed0: 5665 7273 696f 6e3d 2731 2e30 273e 0d0a Version='1.0'>..
00009ee0: 2020 3c74 7275 7374 496e 666f 2078 6d6c <trustInfo xml
00009ef0: 6e73 3d22 7572 6e3a 7363 6865 6d61 732d ns="urn:schemas-
00009f00: 6d69 6372 6f73 6f66 742d 636f 6d3a 6173 microsoft-com:as
00009f10: 6d2e 7633 223e 0d0a 2020 2020 3c73 6563 m.v3">.. <sec
00009f20: 7572 6974 urit
Part of the end of the file was missing - part of the manifest.
For this reason, I decided to check if other elements are missing or if there are any that are damaged. So I did a file inspection in the PE-bear tool:
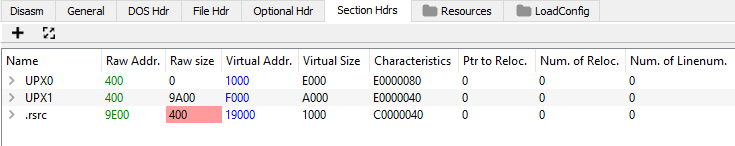
What else did not match? Garbage.exe was 0x9F20 bytes. The offset where the last section (.rsrc) begins is 0x9E00. The declared size of this section is 0x400 bytes. So garbage.exe should be 0x9E00 + 0x400 = 0xA200 bytes.
4. Repairing garbage.exe
I proceeded to repair the file. I started by increasing the file size to 0xa200 bytes by adding zero bytes to the end of the file:
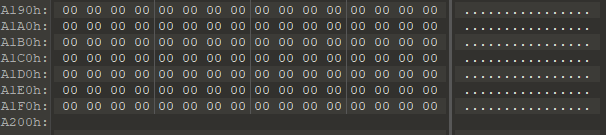
Then, using the 010 Editor tool, I fixed the manifest to its probable form:
<?xml version='1.0' encoding='UTF-8' standalone='yes'?>
<assembly xmlns='urn:schemas-microsoft-com:asm.v1' manifestVersion='1.0'>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v3">
<security>
<requestedPrivileges xmlns="urn:schemas-microsoft-com:asm.v3">
<requestedExecutionLevel level="asInvoker"/>
</requestedPrivileges>
</security>
</trustInfo>
</assembly>
Then I unpacked the file:
74wny0wl@whitehatlab-win C:\Users\74wny0wl\Desktop\2_-_garbage
# C:\tools\_Static\UniversalExtractor\bin\upx.exe -d "garbage - extended - manifest.exe" -o unpacked.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2010
UPX 3.05w Markus Oberhumer, Laszlo Molnar & John Reiser Apr 27th 2010
File size Ratio Format Name
-------------------- ------ ----------- -----------
79360 <- 41472 52.26% win32/pe unpacked.exe
Unpacked 1 file.
The attempt to run the unpacked program ended with an error:
74wny0wl@whitehatlab-win C:\Users\74wny0wl\Desktop\2_-_garbage
# .\unpacked.exe
The application has failed to start because its side-by-side configuration is incorrect. Please see the application event log or use the command-line sxstrace.exe tool for more detail.
5. Inspection of unpacked.exe
I opened the file in the PE-bear tool. I noticed that at least the import table is broken:
Hoping to find helpful information, I previewed the file using the PEView tool:
I noticed four important facts:
- There was an IAT in the
.rdatasection, there were entries about imported functions:
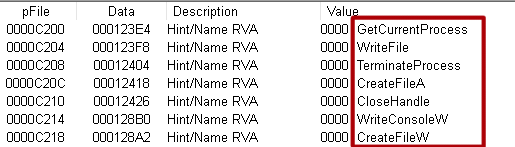
- There were addresses with the names of libraries:
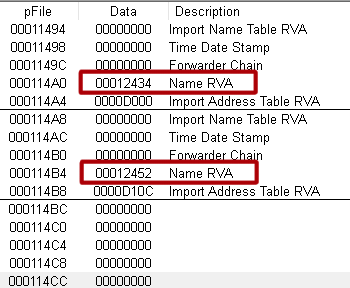
- There was no data under the library names:
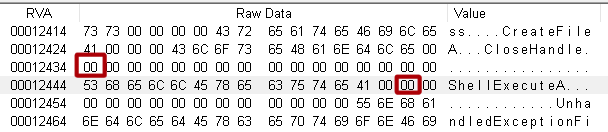
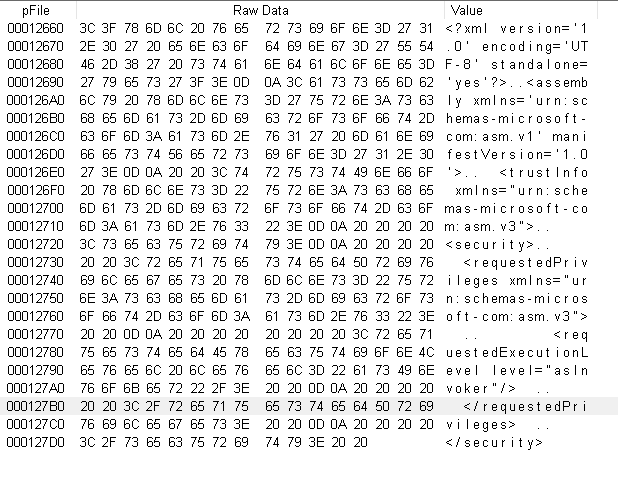
- Again, part of the manifest was missing:
6. Repairing unpacked.exe
I started repairing the import table.
The first names of imported functions found in the IAT allowed for the identification of the libraries used :
GetCurrentProcess - Kernel32.dll
ShellExecuteA - Shell32.dll
By executing the script in python, I calculated the offsets in the unpacked.exe file, which should contain the names of the libraries:
def cast_rva_to_file_offset(rva, section_rva, section_file_offset):
return hex(rva - section_rva + section_file_offset)
rdata_rva = 0xD000
rdata_file_offset = 0xC200
kernel32_rva = 0x12434
shell32_rva = 0x12452
kernel32_file_offset = cast_rva_to_file_offset(kernel32_rva, rdata_rva, rdata_file_offset)
print(kernel32_file_offset)
shell32_file_offset = cast_rva_to_file_offset(shell32_rva, rdata_rva, rdata_file_offset)
print(shell32_file_offset)
I read the result from the standard output:
0x11634
0x11652
Both values were smaller than the address of the next section.data (0x11C00), so they were within the allowed range.
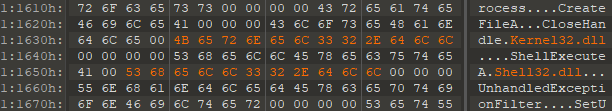
Using 010 Editor I fixed the entries for the libraries used:
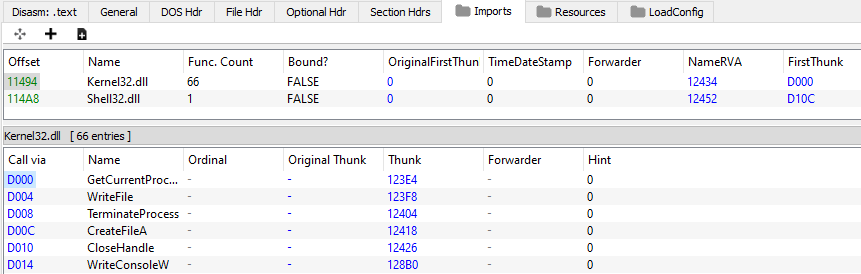
I verified the correctness of the repair performed in the PE-bear tool:
Then, using the Resource Hacker tool, I inserted the correct manifest again:
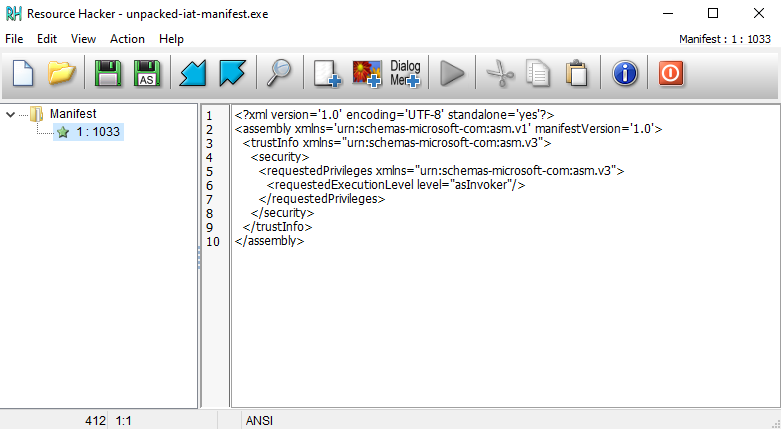
7. Reading the flag
It remains to run the repaired program and read the flag: